In order to complete the Azure AD Connect Cloud Sync deployment, you’ll need to set up a new configuration in the Azure portal:
1.Navigate to the Azure portal (https://portal.azure.com) and select Active Directory | Azure AD Connect.
2. Select Cloud sync from the navigation menu, and then on the Configurations tab, select New configuration.
3. On the New cloud sync configuration page, select which domains you would like to synchronize to Azure AD. If desired, select the Enable password hash sync checkbox. The password hash sync checkbox on this page only enables the feature—it does not configure password hash sync as a sign-in method. See Figure 4.30.
Exam Tip
Azure AD Connect Cloud Sync does not support using password hash sync for
InetOrgPerson objects.
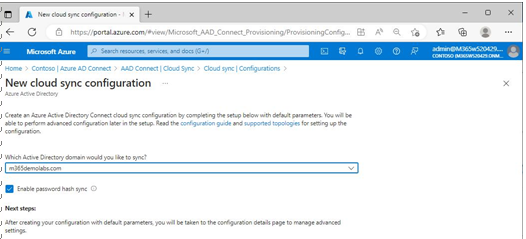
Figure 4.30 – Creating a new Azure AD Connect Cloud Sync configuration
4. Scroll to the bottom of the page and click Create to complete the basic configuration.
The Azure AD Connect Cloud Sync configuration has been completed but it is not yet enabled and ready to start provisioning users. In the next series of steps, you can customize the service before fully enabling it.
Customizing the Provisioning Service
Like the on-premises Azure AD Connect service, Azure AD Connect Cloud Sync features the ability to perform scoping (including or excluding objects from synchronization) as well as attribute mapping.
After creating a new configuration, you should be redirected to the properties of the configuration, as shown in Figure 4.31:
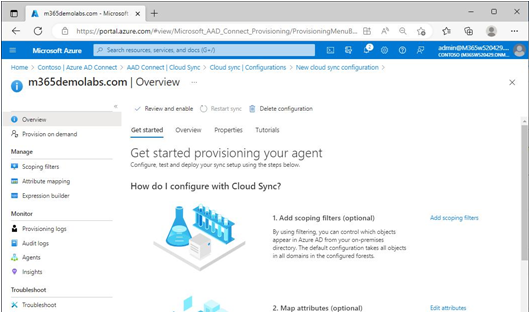
Figure 4.31 – Provisioning agent overview page
From this page, you can set up the scoping filters and attribute mappings for customizing your environment. By default, Azure AD Connect Cloud Sync will include all objects in the connected forest and domains for synchronization.
Scoping Filters
By selecting Scoping filters under Manage, you can configure which objects should be synchronized to Azure AD. You can specify a list of security groups or select organizational units, but not both. See Figure 4.32:
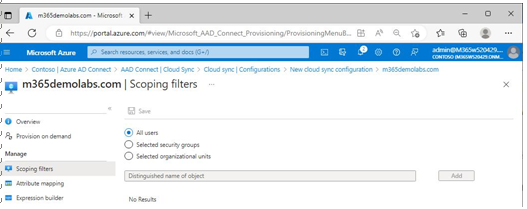
Figure 4.32 – Azure AD Connect Cloud Sync scoping filters
There are a few important caveats when using scoping filters with Azure AD Connect Cloud Sync:
- When using group-based scoping, nested objects beyond the first level will not be included in the scope
- You can only include 59 separate OUs or security groups as scoping filters
It’s also important to note that using security groups to perform scoping is only recommended for piloting scenarios.
Leave a Reply