To enable users to sign in with FIDO2 security keys, you need to configure the authentication policy. Configuring the policy requires an account with the Global Administrator or Authentication Administrator role:
- Navigate to the Azure portal (https://portal.azure.com).
- Select Azure Active Directory | Security | Authentication methods and then select Policies.
- Select Microsoft Authenticator.
- On the Enable and Target tab of the FIDO2 security key settings page, slide the Enable toggle to On. See Figure 5.18:
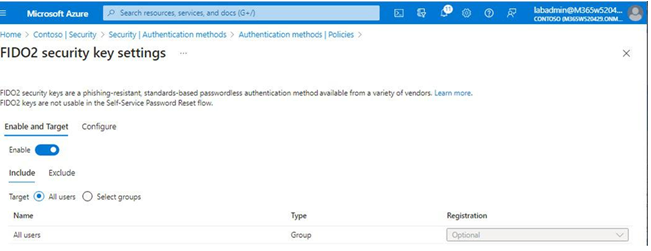
Figure 5.18 – Enabling Microsoft Authenticator
- Using the Include and Exclude tabs, specify which users the policy settings will apply to. Select the All users radio button to include all users in the policy or choose the Select groups radio button to specify which groups will be included or excluded.
- Click Save to update the policy configuration.
The next step is to instruct users to register the security keys.
Registering Devices
Like Microsoft Authenticator-based authentication, FIDO2 authentication requires end users to register the compatible device they wish to use for authentication.
Note
In order to register a FIDO2 security key, the user must already have an Azure AD multifactor authentication method configured. If they do not have one, they must add one (such as Microsoft Authenticator or SMS). If that is not possible, an administrator can issue a Temporary Access Pass (TAP) to allow the user to complete registration. For more information on configuring a TAP, please see https://learn.microsoft.com/en-us/azure/active-directory/ authentication/howto-authentication-temporary-access-pass.
To register a FIDO2 security key, users must follow these steps:
- Navigate to https://myprofile.microsoft.com or, from the Microsoft 365 portal, expand the profile icon and select View account:

Figure 5.19 – Accessing My account
- Click Security Info.
- Select Add method and click Security key.
- Select either USB device or NFC device.
- Ensure the key is ready and click Next.
- In the dialog box, create and enter a PIN for the security key and then perform the required gesture (biometric/touch) to confirm.
- Enter a Name value for the key and click Next.
- Click Done.
After the key has been registered, users can sign in to Azure AD, Entra ID, or Microsoft 365 using their security key. At the sign-in page, after entering a username, users can select the Use Windows Hello or a security key option, which will cause the browser to issue a prompt to insert the key, as shown in Figure 5.20:
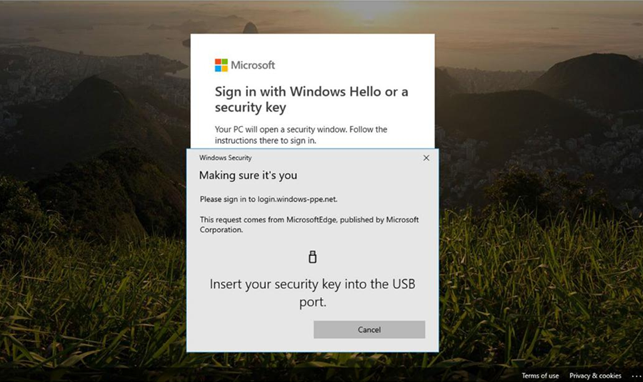
Figure 5.20 – Sign in with Windows Hello or a security key
Next, you’ll look at configuring a self-service password reset.
Implementing and Managing Self-Service Password Reset
Self-service password reset (SSPR) is a feature that allows users to change or reset passwords without administrator or service desk involvement. Self-service passwords can be configured for Azure AD cloud-only environments as well as enabling SSPR of hybrid identity through the Azure AD Connect Password Writeback feature.
Leave a Reply