In addition to the core options for the methods and types of multifactor authentication, Azure AD also supports a number of settings, as given in Table 5.3, to further modify the behavior of multifactor authentication. These properties are located under Azure Active Directory | Security | Multi-Factor authentication in the Azure portal:
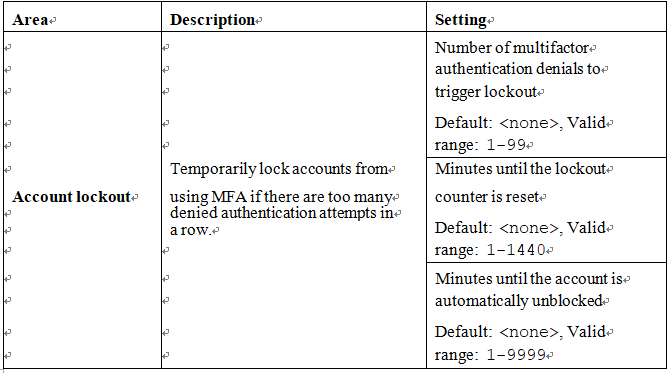
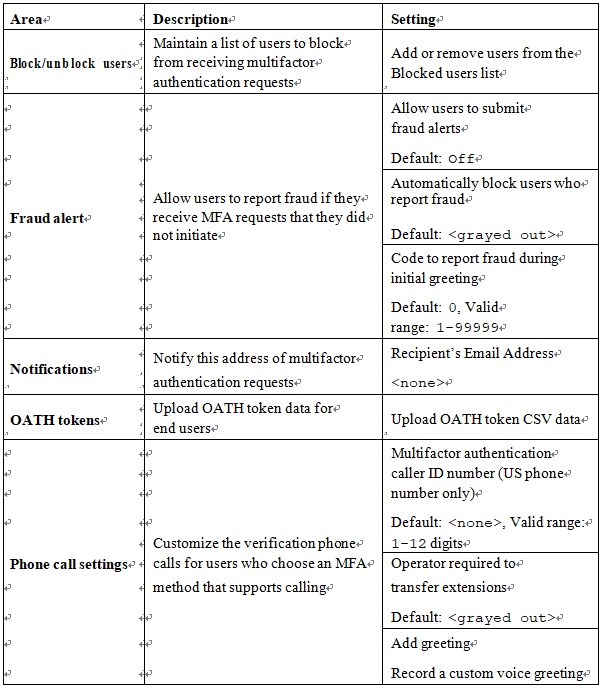
Table 5.3 – Additional multifactor authentication settings
Investigating and Resolving Authentication Issues
Resolving authentication issues in Azure AD can be tricky due to the number of authentication methods, sign-in methods, and other configurations that may be put in place.
The first step when attempting to troubleshoot an issue is to review any available sign-in logs in the Azure portal. To locate the sign-in logs, navigate to the Azure portal (https://portal.azure. com) and then select Azure Active Directory | Sign-in logs. See Figure 5.30:
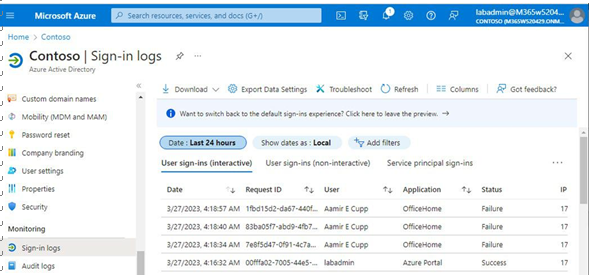
Figure 5.30 – Sign-in logs
Each authentication failure generates an individual entry. You can select an entry to see expanded details, as shown in Figure 5.31:
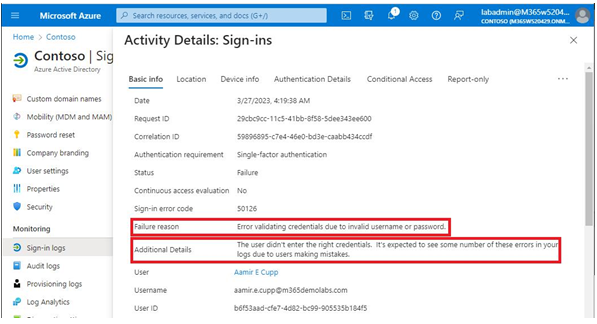
Figure 5.31 – Activity details
The Basic info tab displays high-level information about this particular event. The critical piece of information will typically be listed next to Failure reason, and some expanded explanation may be available in the Additional Details property. In the example shown in Figure 5.31, the reason for the failure of authentication is that the user entered an incorrect password. If the user has entered an incorrect password multiple times in a row, it may be a sign of a forgotten password or an attempted identity breach. Figure 5.32 shows the same account after it has met the smart lockout threshold:
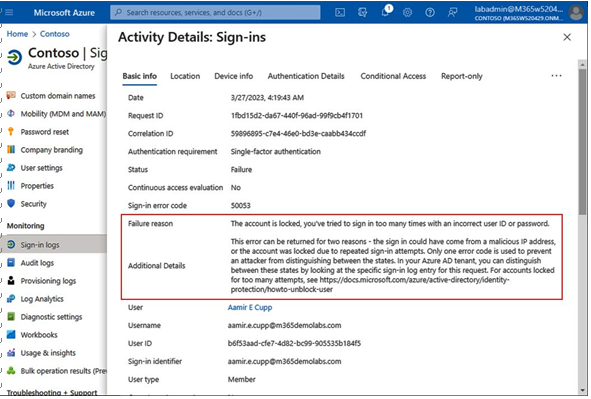
Figure 5.32 – Sign-in detail showing locked-out account
The Location tab will show detailed information regarding the source IP address, and, if possible, resolution to a particular geographic location.
The Device info tab displays information regarding the device that was attempting a logon, such as a Windows 10 device with the Edge browser.
Note
Other browsers can also provide device information or interact with the Microsoft 365 logon process if they have the Windows Accounts extension installed. For example, Chromium-based browsers can install the Windows Accounts extension from the Chrome Web store: https://chromewebstore.google.com/detail/windows-accounts/ ppnbnpeolgkicgegkbkbjmhlideopiji.
The Authentication Details tab, shown in Figure 5.33, provides additional information regarding the authentication method, including whether the user is configured for Password Hash Sync, Federation, or Pass-through Authentication, or whether they’re using a cloud-managed identity:
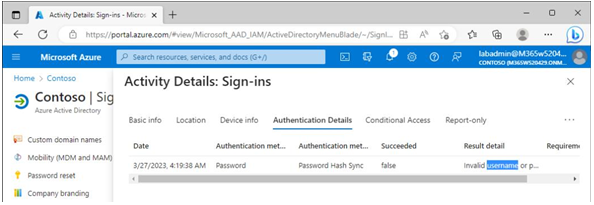
Figure 5.33 – Authentication details
Finally, the last two tabs, Conditional Access and Report-only, show what policies took effect during the sign-in process. You can review these tabs for the status of Conditional Access policies, showing either what was applied or would have been applied during the logon process and how any conditions were satisfied.
Resolving an authentication issue sometimes requires examining several logs to determine the source of the error. In many cases, however, the detailed data provided on each of the tabs of an event’s activity details should provide adequate information to pinpoint the source of the error.
Leave a Reply