Azure AD Connect has a long history, originally starting as DirSync to support the deployment of Microsoft Business Productivity Online Suite (BPOS) in 2007.
If you are familiar with Microsoft Identity Manager(MIM), you’ll notice a lot of similarities shared with the current Azure AD Connect platform. Azure AD Connect (rebranded as Microsoft Entra Connect) allows you to connect to multiple directory sources and provision those objects to Azure Active Directory.
Planning and Sizing
Depending on your organization’s requirements for onboarding to Microsoft 365, as well as additional features or services that are included with your subscription, you may want (or need) to enable or configure additional Azure AD Connect features.
Table 4.2 illustrates the features that can be enabled through an Azure AD Connect setup:
| Feature | Description |
| Device writeback | Synchronizes Azure AD-joined devices back to on-premises |
| Active Directory | |
| Directory extensions | Enables the synchronization of additional on-premises attributes |
| Federation | Enables authentication federation with Microsoft AD Federation |
| Services (FS) or PingFederate | |
| Hybrid Azure AD join | Enables on-premises domain-joined devices to be synchronized |
| and automatically joined to Azure AD | |
| Password hash synchronization | Enables the hash of an on-premises password to be synchronized |
| to Azure AD; can be used for authentication, a backup option for | |
| authentication, or leaked credential detection | |
| Pass-through authentication | Authentication method where passwords are validated on-premises |
| through the Azure AD Connect service’s connection to Azure | |
| Service Bus | |
| Unified group writeback | Enables cloud-based Microsoft 365 groups to be written back to |
| on-premises Active Directory | |
Table 4.2 – Azure AD Connect features
There are several additional features available post-installation for Azure AD Connect, such as managing duplicate attribute resiliency and user principal name soft-matching, both of which are used to manage how Azure AD handles conflicts and connecting cloud accounts to on-premises accounts.
Further Reading
More detailed information about Azure AD Connect’s optional features, such as duplicate attribute resiliency, is available here: https://learn.microsoft.com/en-us/azure/ active-directory/hybrid/how-to-connect-syncservice-features.
Installing the Synchronization Service
The first step to deploying Azure AD Connect is gathering the requirements of your environment. These requirements can impact the prerequisites for deployment (such as additional memory or a standalone SQL Server environment). As part of the planning process, you’ll also want to identify which sign-in method will be employed (password hash synchronization, pass-through authentication, or federation).
Exam Tip
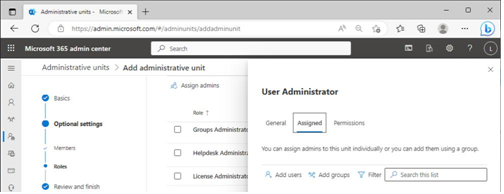
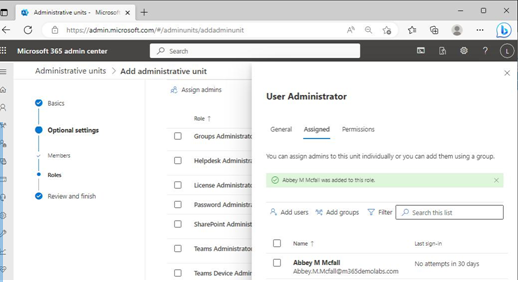
To perform the express installation, you’ll need Enterprise Administrator credentials to the on-premises Active Directory forest so that the installer can create a service account and delegate the correct permissions. You’ll also need an account that has either the Global Administrator or Hybrid Identity Administrator role in Azure AD, which Azure AD Connect will use to create a cloud sync service account.
With that information in hand, it’s time to start deploying Azure AD Connect:
1. On the server where Azure AD Connect will be deployed, download the latest version of the Azure AD Connect setup files (https://aka.ms/aad-connect) and launch the installer.
2. Agree to the installation terms and select Continue. See Figure 4.4:
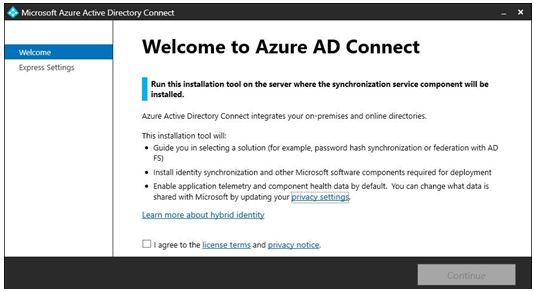
Figure 4.4 – Azure AD Connect welcome page
3. Review the Express Settings page, as shown in Figure 4.5. You can choose Customize if you want to configure Azure AD Connect to use pass-through or federated authentication methods, group-based filtering, or a custom SQL Server installation. While the sign-in methods and other features can be changed after installation, it is not possible to enable group-based filtering or change the SQL Server location after setup.
Figure 4.5 – Azure AD Connect Express Settings page
Installation Notes
If you have other domains in your Active Directory forest, they must all be reachable from the Azure AD Connect server or installation will fail. You can perform a custom installation to specify which domains to include in synchronization.
4. On the Connect to Azure AD page, enter credentials for either the Global Administrator or Hybrid Identity Administrator role in Azure AD. Click Next.
5. On the Connect to AD DS page, enter Enterprise Administrator credentials and click Next.
6. Verify the configuration settings. By default, the Exchange hybrid scenario is not enabled. If you have an on-premises Exchange environment that you will be migrating to Microsoft 365, select the Exchange hybrid deployment option to include the Exchange-specific attributes. If you want to perform additional configuration tasks prior to synchronizing users, clear the Start the synchronization process when configuration completes. checkbox.
Figure 4.6 – Azure AD Connect Ready to configure page
7. Click Install.
8. Review the Configuration complete page, as shown in Figure 4.7, and click Exit:
Figure 4.7 – Azure AD Connect Configuration complete page
If you selected the Start the synchronization process when configuration completes checkbox, you can review the Azure AD portal to verify that users have been synchronized.