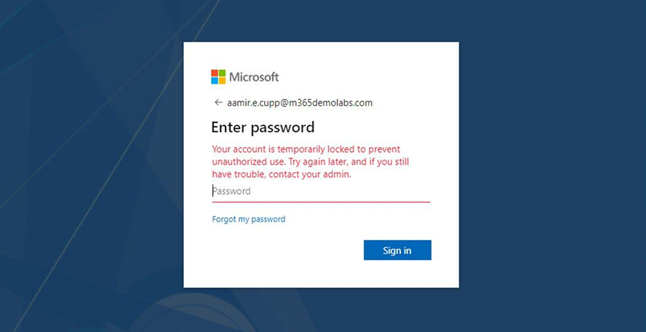
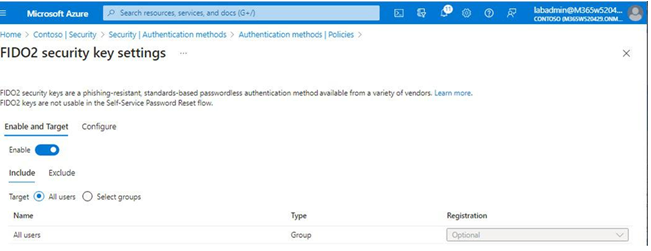
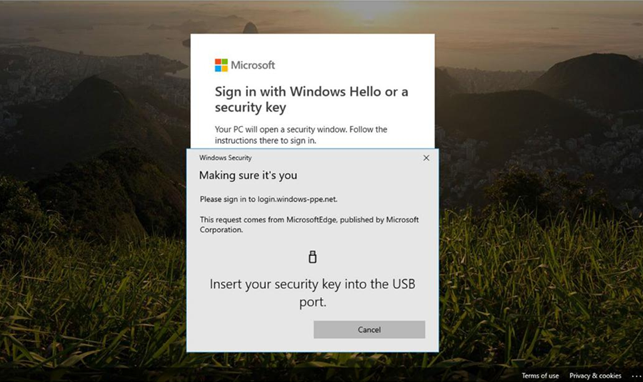
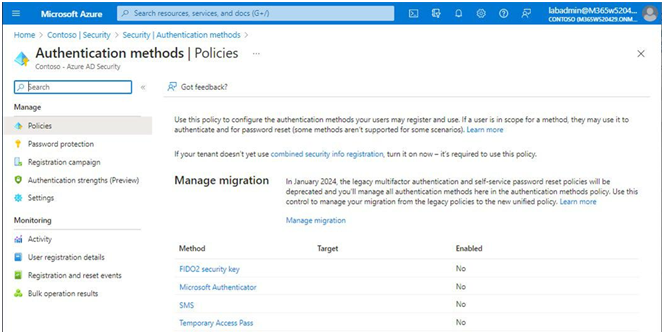
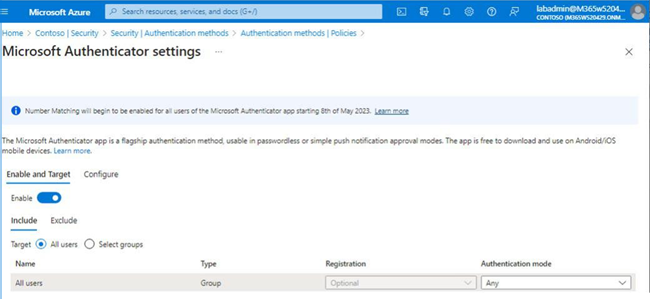
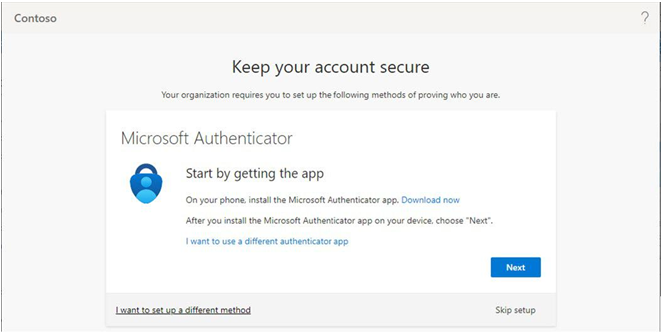
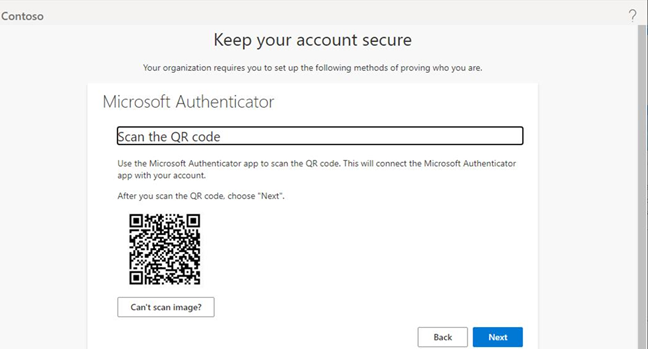
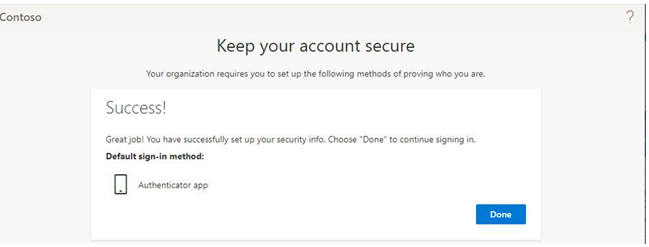
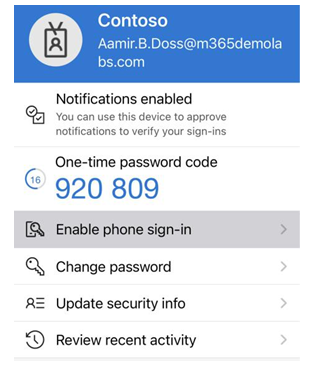
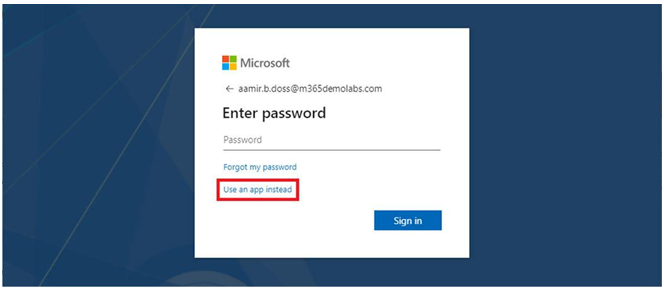
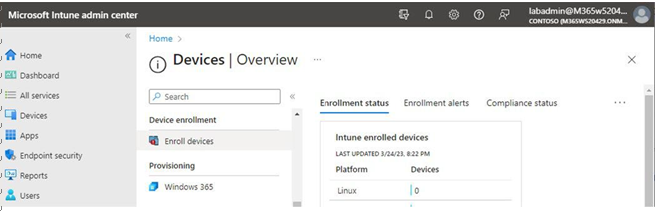
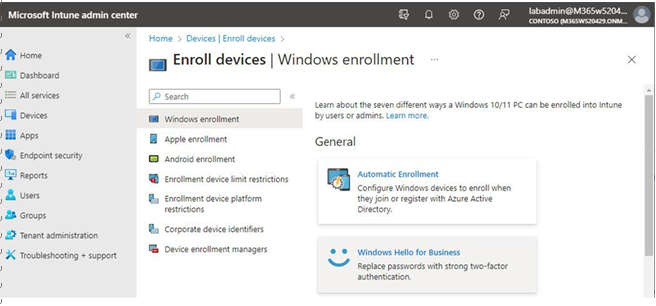
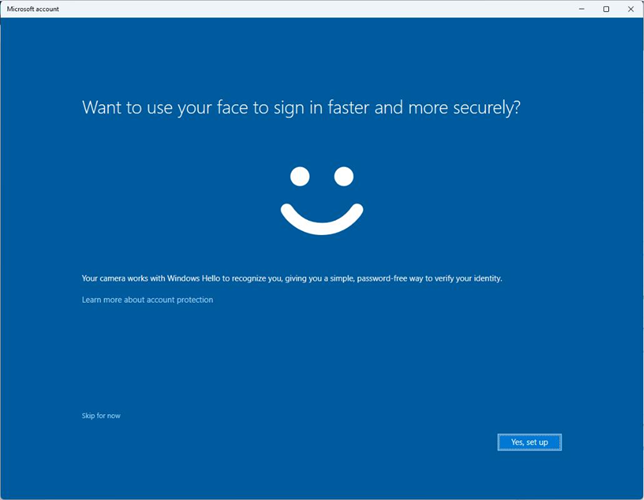
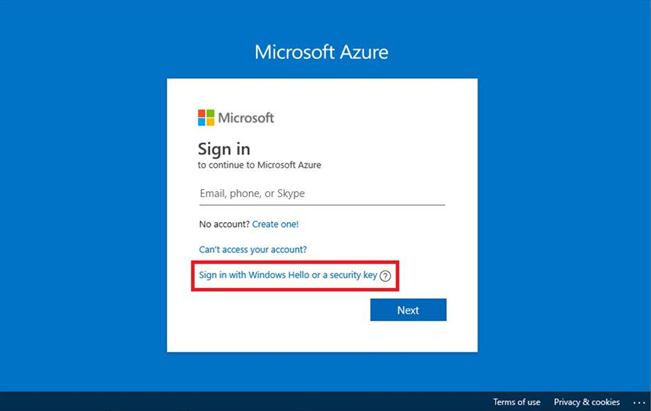
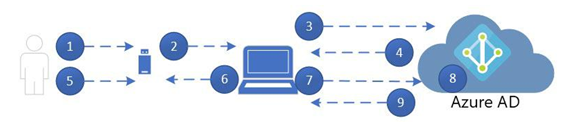
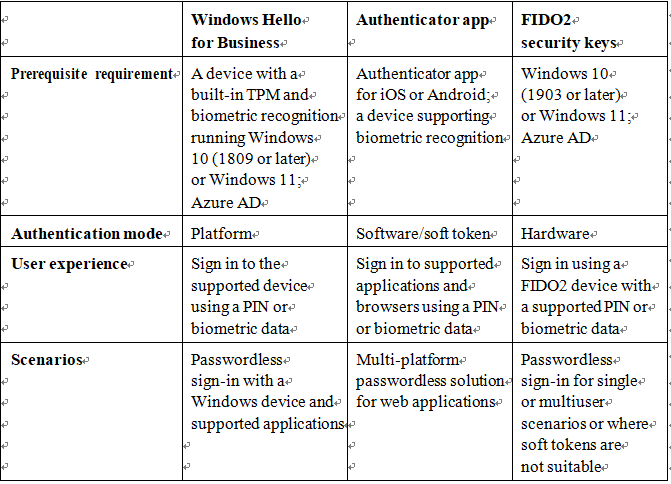
In this chapter, you learned how to evaluate passwordless sign-in options for your organization and deploy the ones that best suit your needs. Some passwordless options, such as Windows Hello or FIDO2 keys, may require specialized hardware such as cameras, USB devices, or fingerprint readers, while the Microsoft Authenticator app method requires only the Microsoft Authenticator app on any supported Android or iOS-based device.
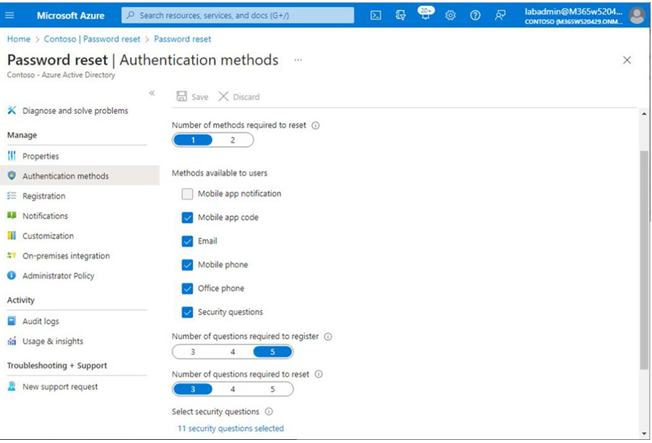
You also learned about deploying features such as self-service password reset and Azure AD password protection to further reduce administrative overhead, helping your organization comply with security policies.
In the next chapter, you’ll learn about implementing secure access in the context of Microsoft 365.
Exam Readiness Drill – Chapter Review Questions Benchmark Score: 75%
Apart from a solid understanding of key concepts, being able to think quickly under time pressure is a skill that will help you ace your certification exam. That’s why, working on these skills early on in your learning journey is key.
Chapter review questions are designed to improve your test-taking skills progressively with each chapter you learn and review your understanding of key concepts in the chapter at the same time. You’ll find these at the end of each chapter.
Before You Proceed
You need to unlock these resources before you start using them. Unlocking takes less than 10 minutes, can be done from any device, and needs to be done only once. Head over to the start of Chapter 7, Managing Security Reports and Alerts by Using the Microsoft 365 Defender Portal in this book for instructions on how to unlock them.
To open the Chapter Review Questions for this chapter, click the following link:
https://packt.link/MS102E1_Ch05. Or, you can scan the following QR code:

Figure 5.34 – QR code that opens Chapter Review Questions for logged-in users
Once you login, you’ll see a page similar to what is shown in Figure 5.35:
Figure 5.35 – Chapter Review Questions for Chapter 5
Once ready, start the following practice drills, re-attempting the quiz multiple times:
Exam Readiness Drill
For the first 3 attempts, don’t worry about the time limit.
ATTEMPT 1
The first time, aim for at least 40%. Look at the answers you got wrong and read the relevant sections in the chapter again to fix your learning gaps.
ATTEMPT 2
The second time, aim for at least 60%. Look at the answers you got wrong and read the relevant sections in the chapter again to fix any remaining learning gaps.
ATTEMPT 3 The third time, aim for at least 75%. Once you score 75% or more, you start working on your timing.
Tip You may take more than 3 attempts to reach 75%. That’s okay. Just review the relevant sections in the chapter till you get there.
Working On Timing
Target: Your aim is to keep the score the same while trying to answer these questions as quickly as possible. Here’s an example of how your next attempts should look like:
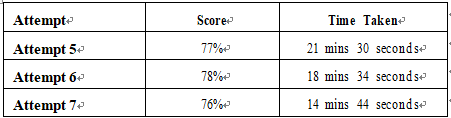
Table 5.4 – Sample timing practice drills on the online platform
Note
The time limits shown in the above table are just examples. Set your own time limits with each attempt based on the time limit of the quiz on the website.
With each new attempt, your score should stay above 75% while your time taken to complete should decrease. Repeat as many attempts as you want till you feel confident dealing with the time pressure.